Hacker food
Why do so many hacker technologies relate to food? Let’s take a look at some of these terms and see why hackers seem to be eternally hungry.
Pineapple
You duck into a coffee shop, laptop slung over your shoulder, and you’re delighted to see the sign that proclaims Free WiFi! As you wait for the barista to prepare your order, you slip into a chair and pop open your laptop. You click your WiFi icon and scan the list of available networks, and choose the top one called Coffee Shop WiFi. All is good.
Not so fast. The network you just connected to could be a pineapple, lurking in the shadows at the next table.
A pineapple is a device designed to pose as a WiFi router. You inadvertently connect to the pineapple, which routes your traffic on to the real WiFi network, but not before capturing all your traffic as it passes through. The pineapple is so named because of its antennae, which supposedly resemble the crown of a pineapple fruit.

Pineapples were first developed as tools for cybersecurity pros to test the integrity of their own networks. But with easy availability at prices under $200, pineapples have become popular with hackers.
Whenever you connect to a network outside your trusted home and office networks, always make sure you’re connecting to the right one. If you’re at Pete’s Coffee Shop, for example, the network is probably called something similar, and not a generic name like “Coffee Shop WiFi”. When in doubt, ask.
At the very least, when you’re at a coffee shop, don’t log into your bank’s website or do other financially sensitive work on the chance that a pineapple is listening. But if all you’re doing is surfing Reddit, you’re probably fine.
Raspberry Pi
A Raspberry Pi is a very small computer that has all kinds of uses, from education to powering robotic arms. A Raspberry Pi is not to be confused with a raspberry pie, which you can eat. It is not advisable to eat a Raspberry Pi.

The Raspberry Pi computer doesn’t have a monitor or keyboard or mouse, but you can connect these things to it if you really want to. (And the second word really is spelled pi, like the mathematical number.)
The Raspberry Pi is popular with schools because a single module can cost as little as $100, making it an attractive option for schools teaching electronics, robotics, and computer-building. The low price point also makes the Raspberry Pi desirable to engineers and hackers as a device for driving various types of devices such as light displays or small motors.
In fact, if the hacker at the next table is running a pineapple, there’s a good chance the pineapple is connected to a Raspberry Pi.
Hash
Corned beef hash, hash browns… the internet is rife with recipes for hash dishes. All of them look delicious, but that’s not the type of hash we’re talking about here.
In cybersecurity, a hash is mush of numbers and letters created from a file. The file is run through a hashing algorithm, and the result is called a hash. The hash is generally much smaller than the original input, and is also nearly impossible to reverse-engineer.
This video gives a great overview of how hashing is used to protect passwords.
(And yes, that’s Michele in an orange wig, having a little fun. There was red wine involved, thus the peculiar color of Svetlana’s tongue.)
Salt
What’s hash without a little salt? In cybersecurity, a salt adds a little spice to a password to make it harder to crack.
When a hacker steals a list of passwords, usually what they get is a list of hashes. This might seem secure, since hashes are impossible to reverse-engineer. But what hackers do is make up a list of hashes of popular passwords, and store each hash in a table with the original passwords. When hackers steal a list of hashes, they just have to look up the hash in the table to find many lame passwords like the ever-popular 1234546 and passw0rd. Animal names like dolphin and monkey are also on the list. This table of hashes and their corresponding passwords, unsurprisingly, is called a lookup table.
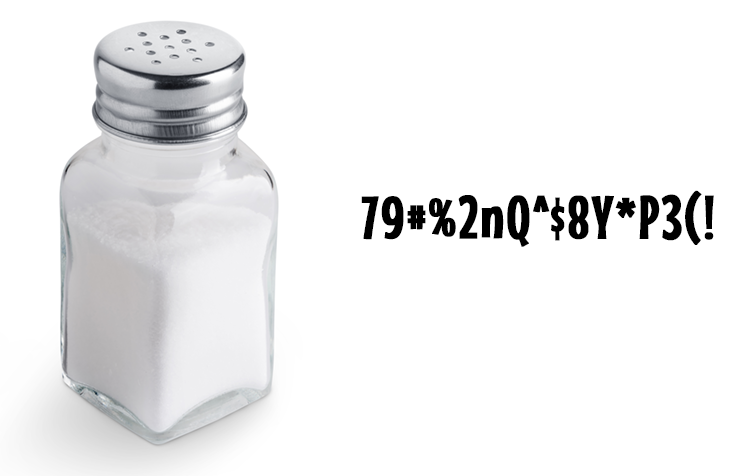
Here comes salt to the rescue! A salt is is a sequence of random characters like 79#%2nQ^$8Y*P3(! that’s appended to a password just before it’s hashed. With such a salt, a lame password like dolphin becomes the very strong password dolphin79#%2nQ^$8Y*P3(! . Even though the salt is often stored in plaintext along with the hash, cracking the hash is much more difficult because the hacker would have to generate a whole new lookup table for all the popular passwords with the salt before she could look up the password. It’s usually not worth it, and the hacker will probably just move on to another password list that isn’t salted.
Sadly, not every company salts their passwords, even though salt is inexpensive and available at supermarkets worldwide.
Be the life of the party
Now you’re ready to get out there and wow your cybersecurity friends at the next party. Amaze them by serving up some hash and insisting they salt it liberally. Ask if anyone brought some Raspberry Pi, and tell them you brought a pineapple but it’s hidden somewhere in the room. It’ll be a laugh a minute!